Atp Sophos
Here you can see the domains and IP addresses that Phish Threat uses to send campaign emails.
- Atp Sophos Utm
- Atp Phospho
- Sophos Atp Logs
- Atp Phosphates
- Atp Phosphorylation
- Atp Sophos Download
- Atp Sophos Free
ATP also uses cloud-based sandboxing, which analyzes suspicious content, so that you can decide whether files are safe to allow. If an attack starts, ATP can prevent devices from connecting to command-and-control servers outside your network. ATP collects data from different sources like DNS etc. You can try to find a C&C Server and resolve his DNS server. Should work, but tbh ATP is not hard to configure:).
The ATP feature in Sophos XG Firewall analyses all network traffic (DNS requests, HTTP requests, or data packets in general), coming and going, for possible threats. The database used to identify threats is updated constantly by a CnC/Botnet data feed from Sophos Labs through signature updates.
Go to Phish Threat > Settings > Sending domains and IPs to review your domains and IP addresses.
You must allow email and web traffic to and from these IPs and domains on your email gateway, web proxy, firewall appliance, or anywhere else in your environment where email and web filtering is done.
You can also find out more about how Office 365 ATP Safe Link and Safe Attachments interact with Phish Threat V2.
This list updates when we add new IPs and domains.

IP addresses
To ensure successful delivery of Phish Threat emails, you must add the following IP addresses to your allow list:
- 54.240.51.52
- 54.240.51.53
Domain names
You must also add the domains listed below to your allow lists.
Atp Sophos Utm
If you're using an external email proxy (including Central Email), you may also need to amend your SPF records.
Links contained within campaign emails are configured to redirect users to an awstrack.me URL. This is expected behavior, as Phish Threat uses AWS tracking to determine which users have clicked on the malicious links.
Atp Phospho
- amaz0nprime.store
- auditmessages.com
- awstrack.me
- bankfraudalerts.com
- buildingmgmt.info
- corporate-realty.co
- court-notices.com
- e-billinvoices.com
- e-documentsign.com
- e-faxsent.com
- e-receipts.co
- epromodeals.com
- fakebookalerts.live
- global-hr-staff.com
- gmailmsg.com
- goog1e-mail.com
- helpdesk-tech.com
- hr-benefits.site
- it-supportdesk.com
- linkedn.co
- mail-sender.online
- memberaccounts.co
- micros0ft.tech
- myhr-portal.site
- online-statements.site
- outlook-mailer.com
- secure-alerts.co
- secure-bank-alerts.com
- shipping-updates.com
- tax-official.com
- toll-citations.com
- trackshipping.online
- voicemailbox.online
- itunes.e-reciepts.co
- sophos-phish-threat.go-vip.co
- go-vip.co
Office 365 ATP Safe Links and Safe Attachments
Office 365 Advanced Threat Protection (ATP) offers security features such as Safe Links and Safe Attachments. Mac os for 7 32 bit.
ATP Safe Links can help protect the organization by providing time-of-click verification of web addresses (URLs) in email messages and Office documents. The ATP Safe Attachments feature checks to see if email attachments are malicious, and then takes action to protect the organization.
If Phish Threat V2 IP address and domain names are not included in the allow list, Office 365 executes the links. This makes it seem like an end user has clicked on the links. To ensure the proper execution of Phish Threat V2 with Office 365, set up an exception for the phish threat for both Safe Links and Safe Attachments in Office 365. For instructions on how to set up these exceptions, see IP addresses and domains.

Other 3rd party email scanning products and Phish Threat V2
Other 3rd party email security products may apply their own scanning techniques that open links and attachments in emails as they are processed. If this is the case you may receive reports indicating that your users have clicked links.
Please make sure the above IPs and domains are added to allow lists within the 3rd party product.
Sophos Atp Logs
Dazzle dvd recorder hd for mac. We are aware that some 3rd party solutions do not allow their security features to be bypassed in this way. We are actively investigating ways to prevent false positive campaign results caused by 3rd party security products. We hope to include these in Phish Threat in the near future.
Advanced Persistent Threats (or APTs) are a kind of malware that can go undetected for long periods of time, waiting for the opportunity to strike, and leaking out your data secretly. Key sketchup for mac. To help you understand how APTs work, we created an interesting infographic showing the lifecycle of an APT.
Atp Phosphates
The APT lifecycle starts with an entry point on your computer network — perhaps by an infected USB device, a phishing email, or a drive-by download — before it calls home for instructions on what to do next.
Atp Phosphorylation
Once the APT has its marching orders from the command and control (C&C) server, it begins to spread through your network, calling home with interesting data, and hiding itself from detection.
Check out the infographic below by clicking on the image to open it as a PDF for a closer look.
Infographic: Advanced Persistent Threats Uncovered
Atp Sophos Download

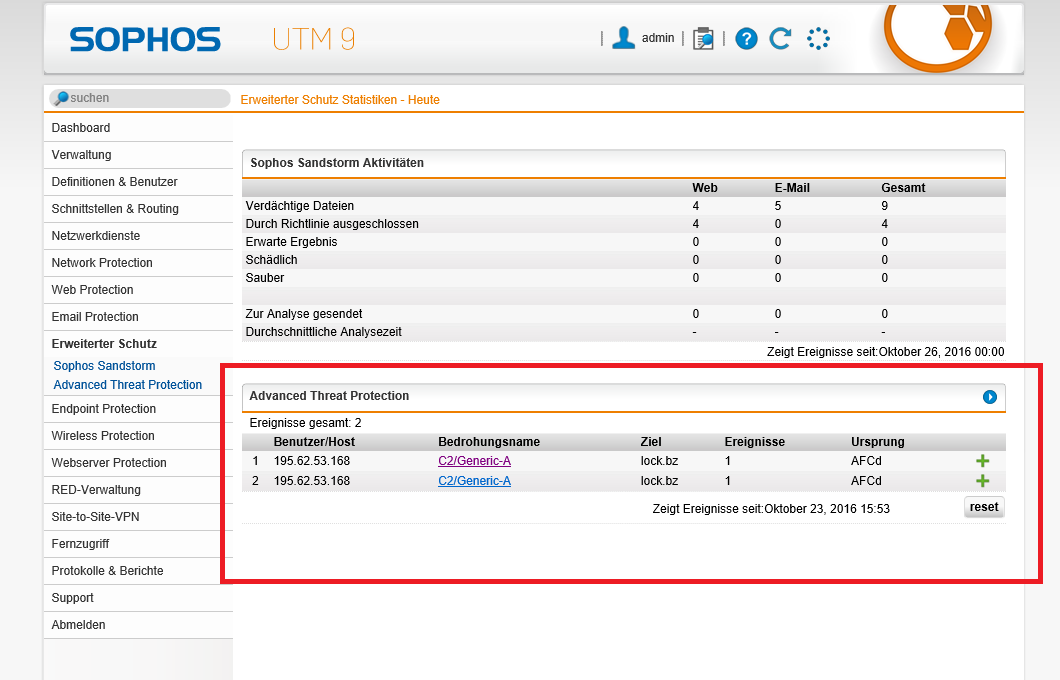
Advanced Threat Protection in UTM Accelerated (9.2)
Advanced Threat Protection in Sophos UTM Accelerated (9.2) is not just a single technology — instead, it provides layers of protection for a defense in depth.
You still need your “standard” protection in place and kept up to date. That means you need the technology to protect you from viruses, email spam, web and other malware, phishing attacks, and more. Those are still the most common tools used in the initial stages of a targeted APT attack.
If you want to find out more about how APTs work and what you can do to protect yourself against them, download our free whitepaper (registration required).
Atp Sophos Free
Presentation (Video): A Pragmatic Approach to Advanced Persistent Threats
Security expert John Shier and senior product specialist Barbara Hudson explore how today’s targeted attacks typically work and what kind of protection is available to help reduce the risk of an attack.
